DATA BREACH #2
Vulnerable website: www.rubberstampchamp.com
Type of breach: Hacking or malware
Data Breach Range: February 4, 2020 to March 24, 2020
Affected Users: approximately 1 million customers (any user accounts created between 2009 and March 24, 2020)
Date(s) Individual Notice Provided to Consumers: NEVER
Was Substitute Notice Given? NO
Was Media Notice Given? NO
Was notification delayed because of a law enforcement investigation? NO
Location of Breached Information: NETWORK SERVER
Type(s) of Personal Information Involved in the Breach:
Vulnerability Details: Security Advisory (NY State - Office of Information Technology Services)
Brief description of the breach:
Unauthorized persons gained root access to rubberstampchamp.com by exploiting a known vulnerability in third-party software. This vulnerability allowed arbitrary code execution with full privileges. Unauthorized persons were able to successfully upload code files and execute them with full privileges, allowing access to all personal and confidential data including all object and source code files, the SQL database and all user data including unencrypted personal and financial information. In addition, after access was gained to the server, a live attack was engineered, in order to capture credit card data as it was being typed in by a customer, which was then sent by javascript to a remote website owned or operated by the hacker. After the malicious software was found and reported to Connectweb by Tom of Anchor Rubber Stamp & Printing Co., Inc., the attacks were mitigated by custom server software built by Matthew Power, which immediately disabled any newly uploaded code files, preventing their execution until the vulnerable third-party software could be patched on all affected websites (approximately 300 websites belonging to 225 businesses).
Offenses against the public:
Connectweb Technologies, Inc. - provider of hosting and information security services for Rubber Stamp Champ - knew about the vulnerability and did not contact the 1 to 3 million affected or likely affected customers by postal mail as required by state law, just as they had failed to notify customers for the prior breach in 2015, which also affected www.rubberstampchamp.com.
Rubber Stamp & Button Champ (a sole proprietorship) and Rubber Stamp Champ, Inc. (a domestic California corporation) knew about the vulnerability affecting or likely affecting hundreds of thousands of its customers and did not notify those customers by postal mail as required by state law, just as they had failed to do for the data breach of 2015.
Rubber Stamp & Button Champ and Rubber Stamp Champ, Inc. did not notify the Attorney General of California about the breach affecting more than 500 California residents as required by CA state law.
By failing to notify affected customers of the data breach, both Connectweb Technologies, Inc, and Rubber Stamp & Button Champ/Rubber Stamp Champ, Inc. owe the state of California the maximum penalty of $250,000 each.
Immanent Risk to National Security of the United States
Connectweb Technologies, Inc. took extraordinary steps to cover up the data breach and attempted to tarnish the pristine reputation of expert software engineer, Matthew Power, who witnessed the data breach, mitigated the breach, patched the breach, assisted the FBI, and urged Connectweb to follow all federal and state laws regarding the notification of affected customers. When Connectweb refused to follow federal and state laws, Power became a whistleblower for the government, as it was known to him that many thousands of government employees and active military personal were affected by this vulnerability, which presented an immanent risk to national security.
The Coverup and Willful Violations of State and Federal Laws:
Connectweb covered up the data breach, retaliated against Power, ended their business relationship, and started embezzling monies due to Power for his co-authorship of Custom Vantage Web. After Power filed a federal lawsuit against Connectweb Technologies, Inc. to recover the unpaid royalties due to him, Connectweb and Rubber Stamp Champ conspired, through use of their legal counsel, to frame Matthew Power for several murders, even trying to name Power as the most prolific serial killer in United States history with a staggering 111 alleged murders, so that Power would be placed under arrest or involuntarily confined to a hospital in order to miss important court deadlines and hearings.
Several police officers searched Power's apartment for "a 55-gallon drum and human remains" due to the report made by the legal cousel for Connectweb Technologies, Inc. to the Swampscott Police Department. The FBI, in turn, reached out to Power for an in-person interview at the Chelsea Field Office, which Power refused citing the absence of a Proffer Agreement. Power endures ongoing harassment by the Swampscott Police Department due to the seed of suspicion planted by the legal counsel for Connectweb Technologies, Inc. and other defendants.
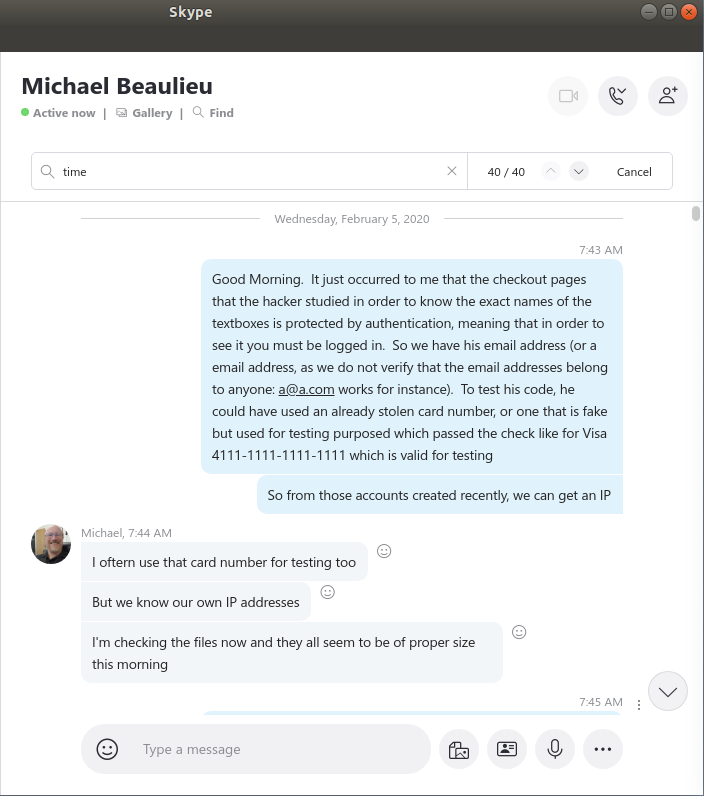
Evidence of Michael Beaulieu's knowledge of the data breach as early as 2/5/2020
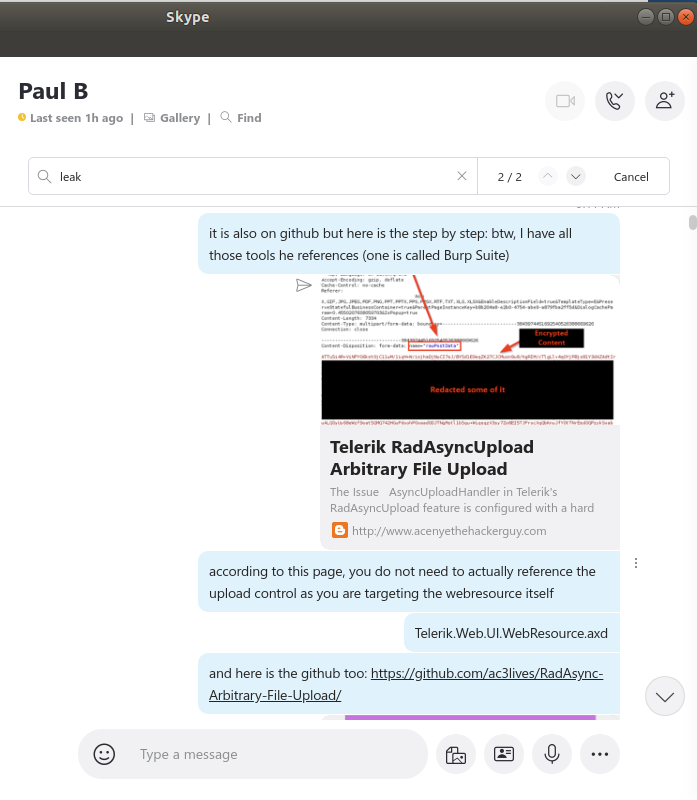
Evidence of Paul Beaulieu's knowledge of the data breach
Evidence of the use of rubberstampchamp.com by various government and military employees (each block is a custom image that was created for reproduction in a nameplate, seal, or rubber stamp by a customer of Rubber Stamp Champ)
